First, we learn about the definition, reasons and importance of data classification before learning the steps to an effective and successful data classification.
♦ Definition of Data Classification:
Data classification is the way of categorizing data into appropriate categories to make it more useful and secure. The classification process makes data easier to identify and recover. Data classification is especially important in data security, risk management, and compliance.
♦ Reasons for Data Classification:
Over time, data classification has considerably improved. Data can be classified for a variety of purposes, including easy accessibility, compliance with regulations, and other corporate or personal goals.
♦ Why is it important to classify data properly and efficiently?
Data protection is not only a legal need in today’s safety context, but it is also crucial to organizational existence and prosperity.
Because storage is low-cost, organizations have become data hoarders. They believe that one day they will be able to mine all of that data for something worthwhile. However, accumulating data can lead to bigger problems. Much of the data collected, which hasn’t even been touched in years, could be duplicated, outdated, insignificant, anonymised, or unknown.
Storage is not free, even if it is cheap. The storage of enormous amounts of data raises costs unnecessarily and, most importantly, endangers your business.
Sensitive data – including information relating to intellectual property, customer or employee identification, such as the social security numbers, financial account information and debit/credit card details, health information, etc., all of which are stored digitally, must be adequately secured.
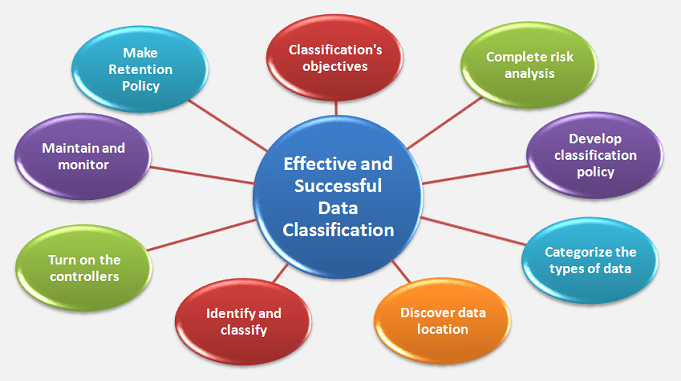
♦ The Steps to an Effective and Successful Data Classification:
Many organizations fail to develop the correct attitudes and expectations, despite the fact that data classification is the basis of any effort to ensure that sensitive data is handled properly. As a result, implementations become too complex and fail to produce useful outcomes. You can classify data efficiently and successfully in the following steps.
1. Determine the classification’s objectives:
Set your data classification targets through an interview-based strategy that includes key stakeholders such as compliance, legal, and business unit leaders. Having a goal will help to assure that the data classification is in the right direction and ensuring that the necessary information is collected and marked.
2. Conduct a risk analysis of sensitive data:
It’s a good idea for a company to assess the risks associated with different sorts of data, how they’re managed, and where they’re stored/sent. Ensure that you are aware of the company’s regulatory and contractual responsibilities regarding privacy and confidentiality.
Data and systems are generally classified into three risk levels.
Low risk: If data is accessible to the public and recovery is easy, this data collection is less risky than others.
Moderate risk: This data includes proprietary operating procedures, cost of goods, and some company paperwork that is used internally by your firm and/or partners or isn’t publicly available.
High risk: This data is extremely difficult to recover if it is lost. All confidential, sensitive, and essential data is classified as high-risk.
3. Develop the classification policy:
Our first priority should be to create a classification policy. Without the proper policy, staying compliant with data protection principles in a company is practically impossible.
To begin, decide who should have access to which types of data. Next, decide on the number of categories you’ll have.
It’s reasonable to use three to four classification categories. Labels that indicate “public,” “internal only,” “confidential,” and “restricted” are good choices. A sample data classification system is shown below: –

As time goes on, more specific labels can be added to it, making sure to explain what each category is and what kind of information. Users can easily decide which label to use because of a simple classification scheme divided into distinct levels and departments.
End-users should classify any newly created and recently accessed data from that day forward after your policy has been developed and distributed.
4. Categorize the types of data:
It can be difficult to figure out what kinds of sensitive data your company has. Organizations can minimize the risk of data loss by categorizing data according to its value or sensitivity, by ensuring that proper precautions are put in place and enforced consistently.
Take each business activity into consideration, tracking data flow provides an insight into what data must be safeguarded and how it should be protected.
It is the unknown data that puts you at risk. Now that you have recognized your most valuable data that needs securing, it is time to start the discovery to find out exactly what data you have, where it is stored, and who has access to it. Even the greatest security plans are useless if you don’t know what data you’re storing.
Consider the following questions need to determine:
• How do you collect and what type of data?
• What data does your company collect from customers and partners?
• How do you create data about them?
• What is the location of the data?
• What kind of proprietary data do you create?
• What kind of transactional data do you handle?
• What data, if any, has been collected or created that is confidential?
• What is their sensitivity level?
• What is the purpose of having them?
• Who has access to, uses, and shares them?
5. Discover your data location:
Now that you have recognized your most valuable data, it is time to do a discovery exercise to determine exactly what data you have, where it is stored, and who has access to it.
It is important to list all the places where data is kept electronically, after setting up the types of data in your company. The flow of data in and out of the organization is an important consideration.
It may be tough to create a centralized database if not impossible since data is likely entered via many different channels in your organization and stored all over the place. Fortunately, there are tools available to assist you in finding and organising your data.
Data discovery tools can aid in the creation of an unstructured data inventory and the understanding of where your company’s data is stored, regardless of structure or location.
Data discovery tools identify and categorise the risk associated with unknown data sources inside an organisation, particularly sensitive data sources.
These tools assist firms in maintaining data compliance, preventing data breaches or loss, and allowing for more efficient sensitive data storage. These tools also aid in the identification of data owners by providing information about users who handle data.
Keywords or certain types or formats of data, such as medical record numbers, social security numbers, or credit card numbers, can be used in your data discovery efforts.
Large corporations and organizations that operate with a lot of sensitive data, such as insurance companies, and others that work with their end-users or customers’ sensitive or proprietary data, should employ sensitive data discovery tools.
6. Data must be identified and classified:
Only after knowing where your data is kept can you identify and classify it so that it can be properly protected.
To begin, you must accept that not all data is created equal. You can wind up wasting valuable resources if you don’t precisely identify which data is the most sensitive and requires the most protection if you use the same security methods for all of your data.
Most corporate data needs strict security measures, yet some data does not require any protection at all. To prevent wasting time and money, it’s critical to define your priorities and optimize your data protection.
Take into consideration the penalties for loss. Knowing the possible costs of a data collection’s breach will help you set expectations for how much it will cost to protect it and what classification level to use.
Commercial classification tools help data classification efforts by making it easier to identify relevant classifications and then applying the classification label to the item’s metadata or as a watermark.
7. Turn on the controllers:
To guarantee that the right solutions are in place, establish baseline cyber security measures for each data classification label and develop policy-based controls. High-risk data needs more advanced methods of protection, and low-risk data requires less. You can build suitable security controls based on associated risks by identifying where data lives and the organizational value of the data.
Classification metadata can be used in encryption, the prevention of data loss, and other security systems to determine what information is sensitive and how it should be protected.
8. Maintain and monitor your Classification Policy:
Be ready to monitor and maintain the data classification system of the organisation and make modifications as required. Policies for classification should be dynamic. To encourage acceptance and ensure that your method continues to suit the changing demands of the business, you should design a review and update process that includes users.
9. Make a Policy on Retention:
Finally, you must determine how long you will retain your data. Not every piece of data requires the same amount of storage time. As a result, you should have a clear retention policy in place for each category. To avoid any legal issues arising from deleted or lost data, make sure to follow all of the rules and regulations.
(Source – Various books of college library)
Copyrighted Material © 2019 - 2024 Prinsli.com - All rights reserved
All content on this website is copyrighted. It is prohibited to copy, publish or distribute the content and images of this website through any website, book, newspaper, software, videos, YouTube Channel or any other medium without written permission. You are not authorized to alter, obscure or remove any proprietary information, copyright or logo from this Website in any way. If any of these rules are violated, it will be strongly protested and legal action will be taken.



Be the first to comment